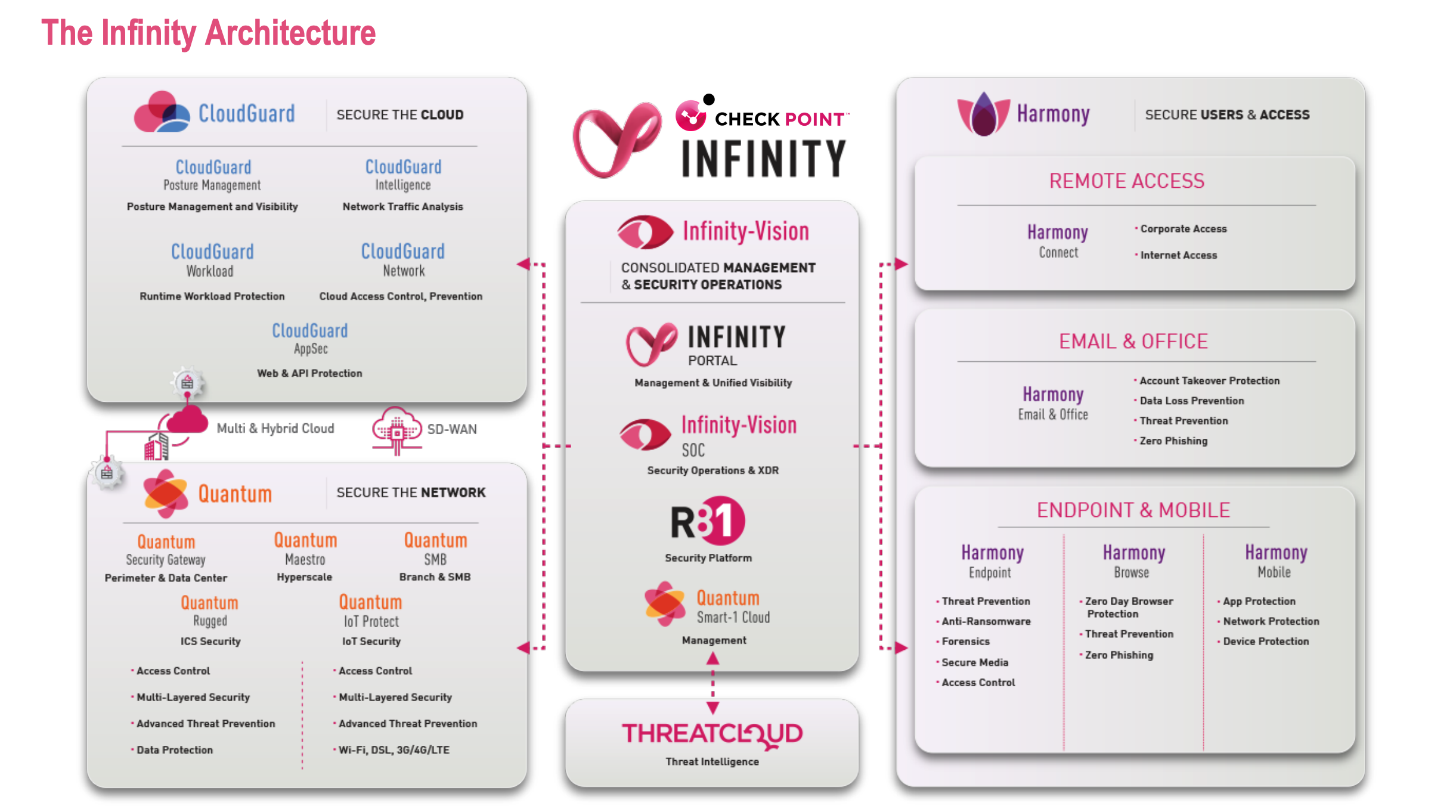
Protect your enterprise network from the most sophisticated cyber-attacks with the highest caliber of security, real-time prevention and the world’s highest performing security gateways.
Quantum: Secure the Network
CloudGuard: Secure the Cloud
Harmony: Secure Users & Access
Horizon: Unified Management & Security Operations
Threatcloud:
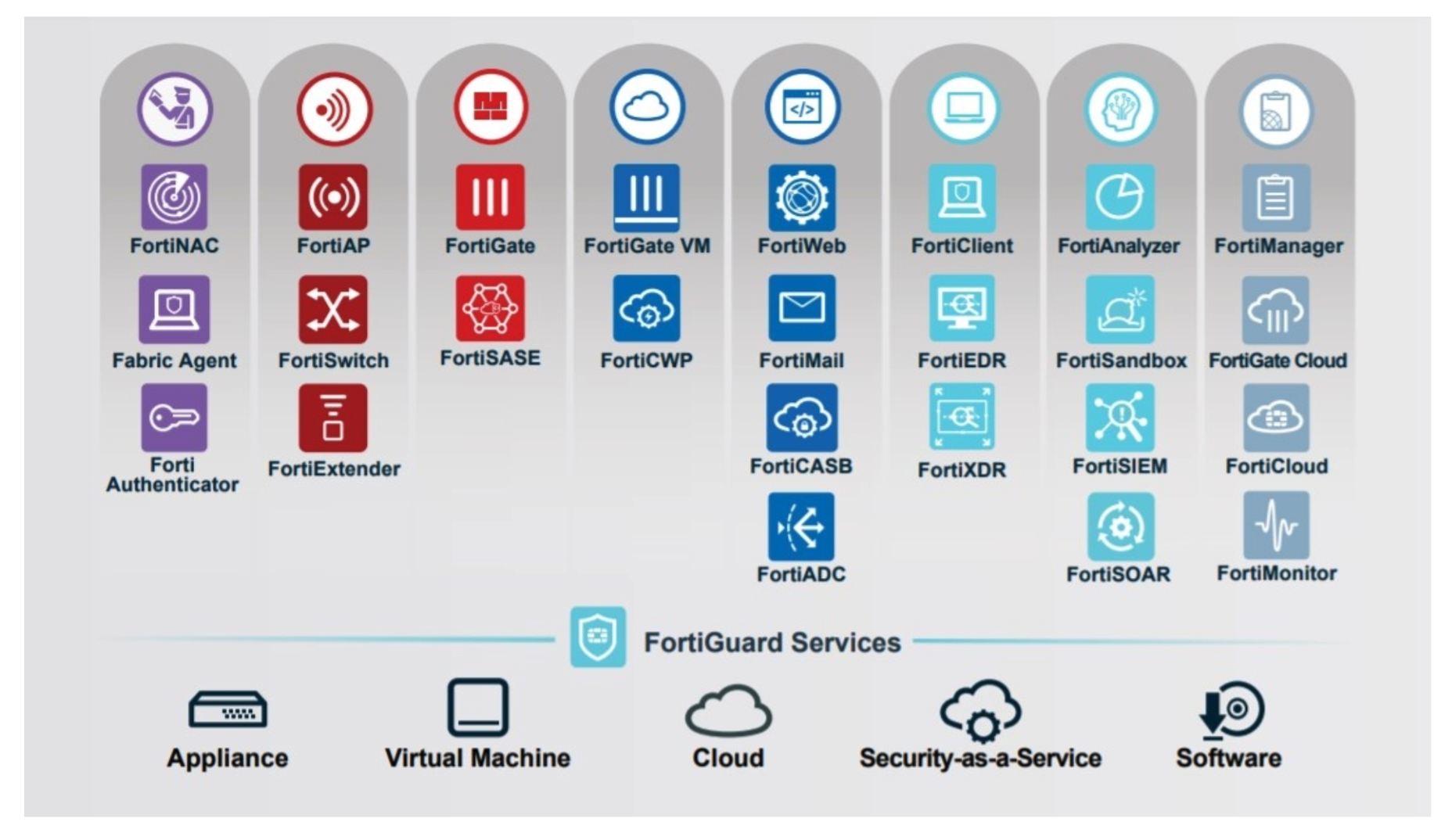
The Fortinet Security Fabric seamlessly integrates convergence and consolidation principles to deliver thorough cybersecurity protection for users, devices, and applications across every network edge.
The Fundamental Pillars of the Fortinet Security Fabric
FortiGuard AI-Powered Security
Secure Networking
User and Device Security
Application Security
Fortinet Fabric Management Centre
Network Operations Center (NOC)
Security Operations Center (SOC)
Open Ecosystem
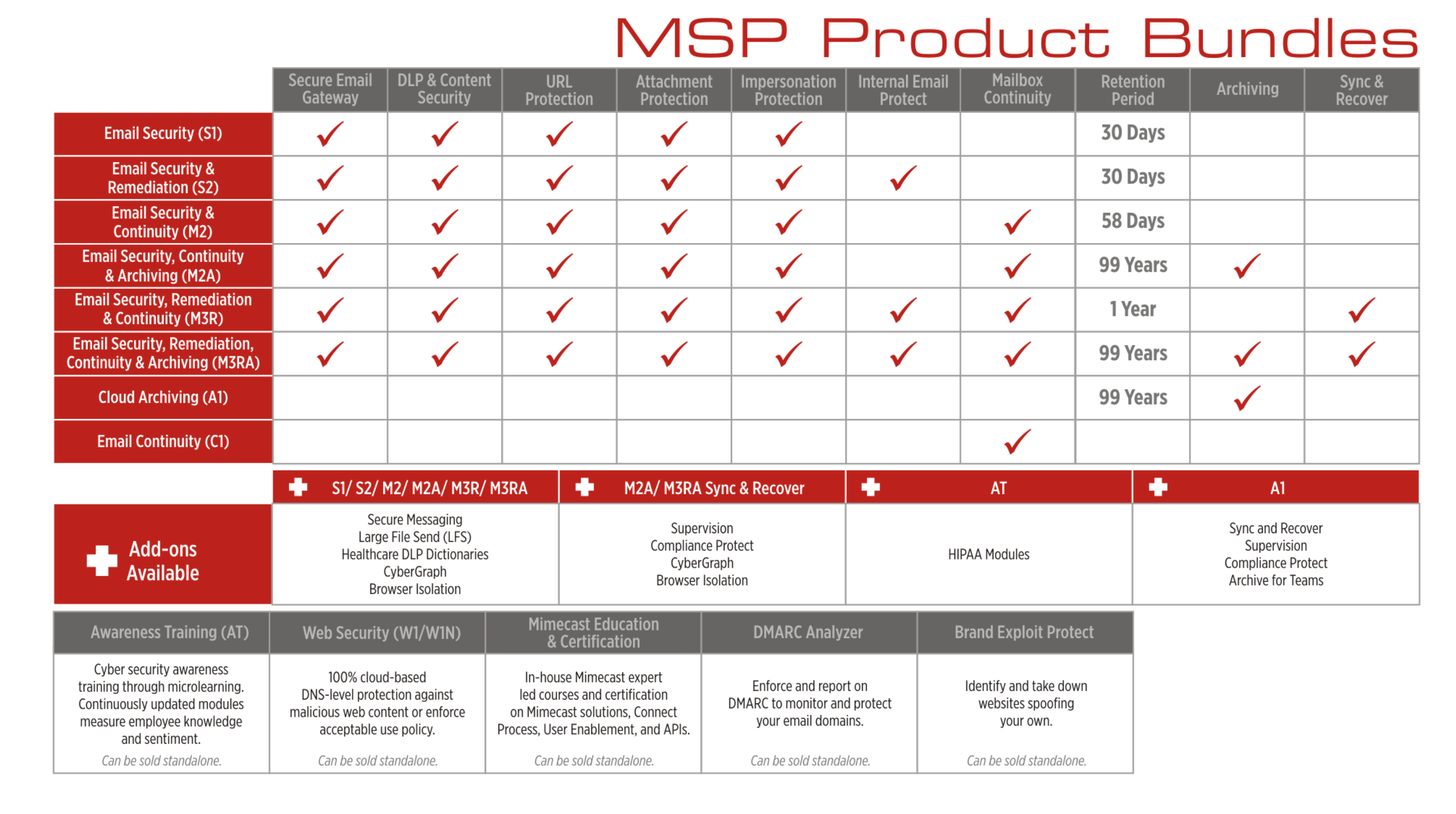
Businesses require cybersecurity solutions that shield against threats and are efficiently managed for reliability, speed, and flexible deployment. Through collaboration with Mimecast, inq. presents an integrated managed service provider offering that exceeds these expectations.
Email Security & Resilience
Data Retention & Compliance
Security Awareness Training & User Behavior
Sendmarc’s DMARC compliance software protects your domain against email phishing and impersonation attacks, safeguarding your staff, clients, and suppliers. DMARC (Domain-based Message Authentication, Reporting & Conformance) reinstates control to the email sender, regardless of the mail’s destination.
Emails play a role in over 91% of network attacks, with cybercriminals becoming increasingly adept at impersonating unprotected email domains. Without protection, they can effortlessly use brands to mimic employees, sending emails with flawless styling, making it nearly impossible for recipients to discern the fraudster. An attack on your business could lead to deposit fraud, ransomware attacks, identity theft, or reputation damage. Sendmarc addresses this vulnerability through DMARC.
How Sendmarc helps: DMARC verifies the source of an email message and determines its fate. It’s a security check that allows only emails from legitimate sources to be delivered. DMARC compliance gives your company full visibility and control over all emails, distinguishing between legitimate and illegitimate ones claiming to be from your organisation. The DMARC standard corroborates the sender’s legitimacy, ensuring the message’s integrity and delivering it to the inbox if it passes authentication while rejecting it if it fails.
Visibility into where email comes from
Strengthen brand trust and brand recognition
Email that is trusted by entire stakeholder community
Provided as a service with zero infrastructure costs
Global and company-wide compliance
Guaranteed for every customer
Improved email deliverability
Protection for the entire email Ecosystem
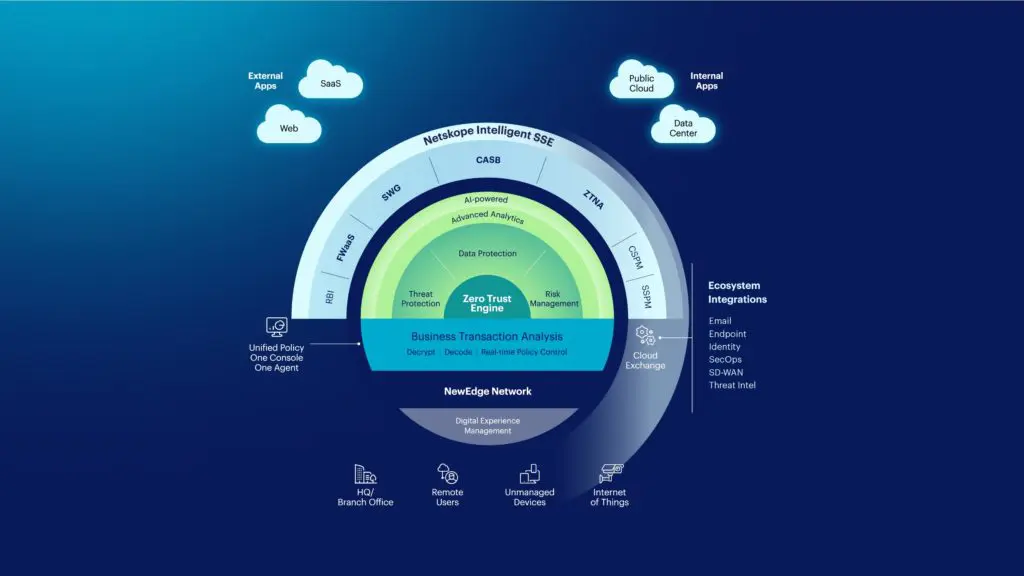
Organisations are swiftly embracing a Secure Access Service Edge (SASE) architecture to ensure data security across its various movements, support digital transformation initiatives, and optimise efficiency and return on investment from their technology. Netskope stands out as a recognised expert and innovator in CASB, SWG, ZTNA, Firewall-as-a-Service, and other Security Service Edge (SSE) components, a term encompassing the necessary security services for a successful SASE architecture.
Netskope addresses these challenges with the Netskope Borderless SD-WAN, combined seamlessly with Netskope Intelligent SSE, forming a fully converged SASE platform. This unique integration ensures comprehensive solutions, mitigating the issues associated with disjointed and inadequately integrated products masquerading as SASE.
Cybersecurity has transitioned from being a luxury to an indispensable business necessity. Nevertheless, deploying comprehensive Security Incident Event Management (SIEM) solutions poses a challenge for many, particularly in an era where specialised expertise is scarce. This challenge is compounded by the high costs and technical complexities associated with implementation and integration into existing environments.
Product Integration
Product Demonstration
Automated Processes
Attain comprehensive insights across all your attack surfaces, spanning networks to endpoints.
Proactive Threat Detection
Identify cyber threats, intrusions, and breaches well in advance.
Efficient Threat Containment and Elimination
Promptly isolate and neutralise identified threats for swift action.
Consistent Compliance and Reporting
Sustain an up-to-date compliance posture and streamline reporting processes.
Effective Security Operations Management
Optimise the efficiency of your security operations, all within a centralised platform.